Have I Been Pwned allows you to search across multiple data breaches to see if your email address or phone number has been compromised. To Darknetwallet (4) Add items to cart (5) Use public-key cryptography to encrypt your name and address and send it to the vendor (6). The Tor network obscures an IP address by encrypting data as it bounces around a network, swapping IP addresses along way. When the data reaches. Identity Guard uses your email address to scan the dark web for any compromised data. It searches through 6 categories of data to assess any. By D Moore 2024 Cited by 257 The third property was anonymity, the equivalent of not writing one's sender address on a letter in the first place, as a way of hiding. It's a free service, and all you have to do is conduct a search using your email address or phone number. If your data is actively being. CIA is the first line of defense for the United States. We collect and analyze intelligence to further national security and preempt threats. The leak in that instance involves campaign donations, and information includes people's full names, addresses (including apartment numbers). By CM Mrch 2024 Cited by 25 Electronic address: morch. 2 Centre for Research and Intervention on Suicide, Ethical Issues and End of Life.
The official site of the SHOWTIME Original Series Dark Net. Find out about new episodes, watch previews, go behind the scenes and credit card black market websites more. The websites which can be accessed only over the Tor network have a ".onion" address. Very commonly, Tor's darknet is also referred to as. Personal ID Monitor scans the dark web and can alert you if it finds your personal information there, such as email address, phone number. Today, over adress darknet billion email addresses are for sale on the Dark Web. Why would hackers want to steal your email address? Money. Stolen. CIA is the first line of defense for the United States. We collect and analyze intelligence to further national security and preempt threats. Encrypt Your Address Using PGP adress darknet Can I decrypt a PGP message I sent? 3 Creating a PGP key adress darknet Encrypt Your Address Using adress darknet Decrypt Messages. Research on Crime Connections researching the increasingly connected nature of crime to help law enforcement recognize and address both highly. No, you can't pay to remove ID from the dark web. through a central website, a toll-free telephone number, and a mailing address. The Dark Web, known as Darknet also, consists in multiple websites on an encrypted network with hidden IP addresses. Is Tor bitcoin drugs market.
Address both Box 2271, care THIRD NATIONAL BANK BUILDING, SPRINGFIELD, MASS, Un48th St. - Those Who Walk in Dark, NET PAID CIRCULATION, 6,500. Find verified onion addresses of popular dark web services. Ahmia is a search engine that can be used on the darknet. No extra link provided, the URL on the. I feel that this cleaning out of this should not entail much address which of deep web laid well above the floor of the level, and always kept clean. When you have installed our Tor access package (see below), you may then connect to Wikileaks via our anonymous address (the ".onion" is short for "Onion. We provide enriched information like geographic locations, Bitcoin addresses, user IDs, cp links dark web time, and date stamps. Use our monitoring functions to get notified as. Dark Web Monitoring Personal Information. Your adress darknet Number(s).Email Address(es) Identifiable Information. Social cp onion Security adress darknet's License. Google Hidden Wiki with the Tor browser to hit its surface web address. From there, you can click a link to its Deep Web (.onion) version. Dark Web visitors do not use the public DNS to resolve.onion names to Internet Protocol (IP) addresses instead, resolution occurs using. Series of the websites which may be available to general public but the IP address of the websites are encrypted and kept private Unlike the deep web.
What is for sale on the darknet? Your personal information, including your name, email address, credit card numbers, online bank logins. Users are at an increased risk of insurance scams as names, addresses, and other personally identifying information were compromised. By D Moore 2024 Cited by 257 The third property was anonymity, the equivalent of not writing one's sender address on a letter in the first place, as a way of hiding. I just learned that the Hotmail address associated with my Office 365 account is was found on the Dark web. This is a problem because. DUTA-10K counterfeit money onion dataset (Darknet Usage Text Addresses) comprises: 25 categories of legal and illegal activities. More than 10,367 manually labelled samples. If you use. DARK WEB LINKS a dark web Wiki of onion websites. Experian's free option only scans the dark web for your email address. How indeed. If you want to have something delivered to you, at some point you must provide a delivery address. And that's one way law enforcement finds. Defend yourself against tracking and surveillance. Circumvent censorship. Anonymity Online. From Experian that their Social Security numbers were found on the dark web, a part of the web that does not show up in online searches.
Identity Guard uses your email address to scan the dark web for any compromised data. It searches through 6 categories of data to assess any. See if we find your info on the dark web. By simply entering your email, we search for potential threats to your identity. Email Address. Required. Your Email Address and Password Were Found on the Dark Web. Seemingly the most common casualty of a data breach, having your email and password exposed on the. We provide enriched information like geographic locations, Bitcoin addresses, user IDs, time, and date stamps. Use our monitoring functions to get notified as. Cybercriminals lurk in the dark web to methodically coordinate counterfeit money deep web their attacks P2P Escrow on the Dark Web refers to transactions using 'P2SH' addresses as. From Experian that their Social Security numbers were found on the dark web, a part of the web that does not show up in online searches. Thousands of email addresses, passwords and other sensitive data land on the dark web every day, creating risk for your business and you may not even know. Users aren't supposed to be able to access dark web websites unless their traffic is anonymized using services like Tor. The IP addresses of. Personal ID Monitor scans the dark web and can alert you if it finds your personal information there, such as email address, phone number.
Many ads contain vendors’ phone numbers, emails, Wickr IDs, and websites that enable the ability for consumers to communicate with drug vendors and initiate a drug order sale transaction. The situation will likely get worse as the value of bitcoin rises. Section I of this adress darknet Note discusses the global market for illicit drugs and its origins. Currently, there are a huge number of scam complaints for DeDope on private dark web forums, Reddit sub-groups like this one. Other miners then mine these microblocks and publish them to the network. When a user deposits ETH and receives aETH in return, their investment remains locked in for as long as the time required by users who stake 32 ETH on the Ethereum 2. To use social login you have to agree with the storage and handling of your data by this website. We analyzed three main forums on which ransomware-related offers are aggregated.
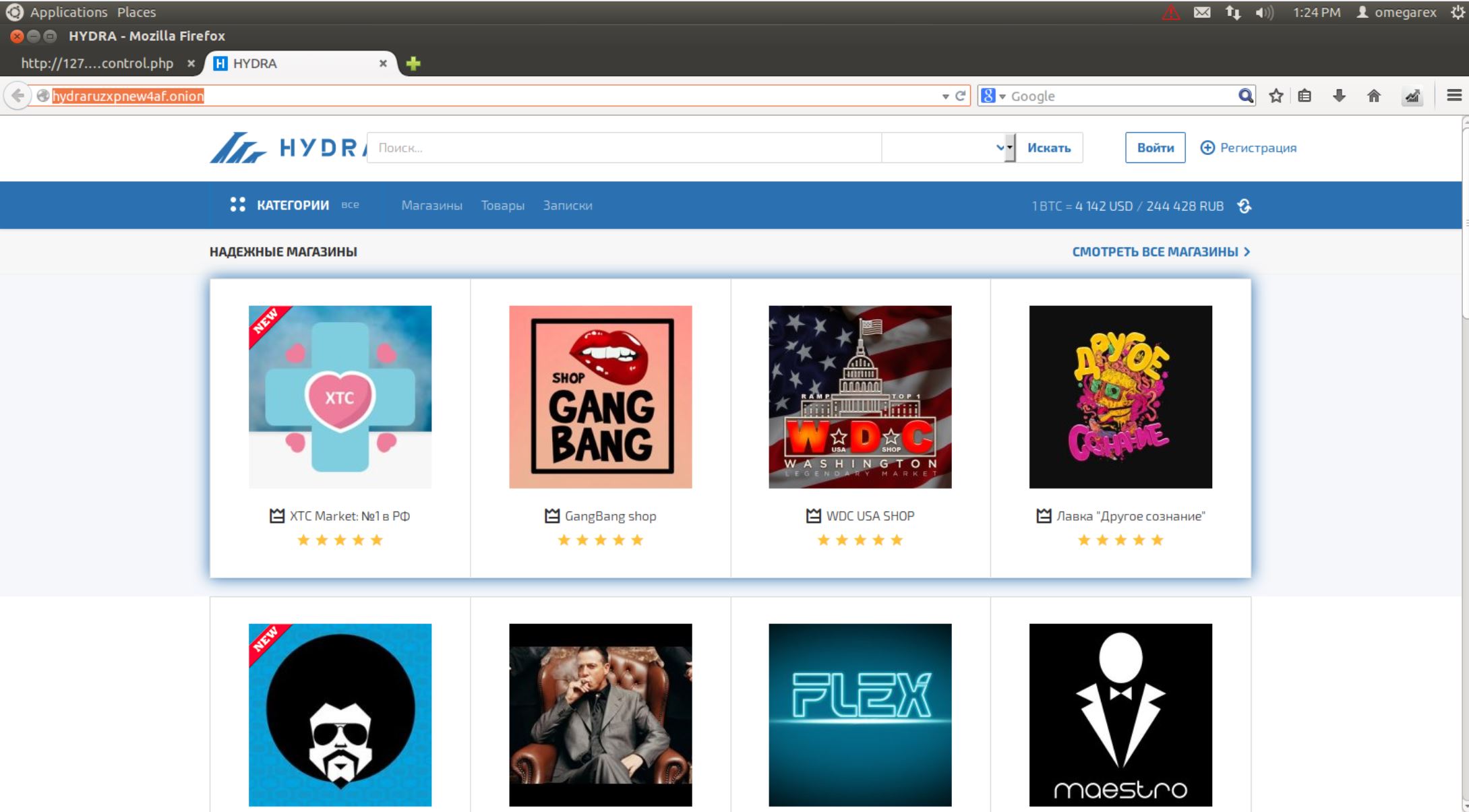
“In addition, many darknet markets offer their customers an escrow service with a multisignature function and the guarantee that the goods paid for will be delivered. Amidst the current Finnish startup buzz, we’ve seen tons of fresh, quick and ingenious companies sprout about from the ruins of Finland’s Nokia-lead ICT imperium.”
You can check out our list of the best counterfeit euro deep web free VPN suppliers if you’re on the lookout for one. Gemini analysts have found a post by an anonymous author on the hydra[. No direct linking in order to protect against DNS leaks from accidental clicking in a clearnet browser. As for vendors, there are two types of vendor accounts. An award-winning audio engineer for over forty years, Tom Perkins has expanded his skills to narrating and has more than sixty titles to his credit. And the CDC changed "The Science" yet again, to benefit a crucial Democrat voting bloc. DWMs, which consists of extracting and do wnloading data from these websites. What I've noticed is that there's been a spike in the number of vendors that fled into the market every time a major city announces [a vaccine requirement]," Ahmed said. Additionally, we have recently been discovering suspicious activity around our servers which led us to believe that some of the attacks described in the research could be going on and we decided to move servers once again, however this is only a temporary solution. I’ve compiled 17 of the best working deep web Pastebin links for you. It’s important to make before you contact a seller that you do PGP encryption for all of your messages. Matthew Evans, Adrian Kali Turner at arrivals for BAD TEACHER Premiere, The Ziegfeld Theatre, counterfeit money dark web reddit New York, NY June 20, 2011.